Dvd,cd,are not use long time and difficult to carry cds .so why not make usb Boot able Pan drive. and work to easy.all Hardwre Engineer.Show how to make Pan driver bootable ,
Once you have the file, you'll need to burn it to a DVD disk or a bootable USB stick. The USB option is often easier, and it means you can carry the stick drive in your pocket if you need to update the PCs of friends and colleagues.
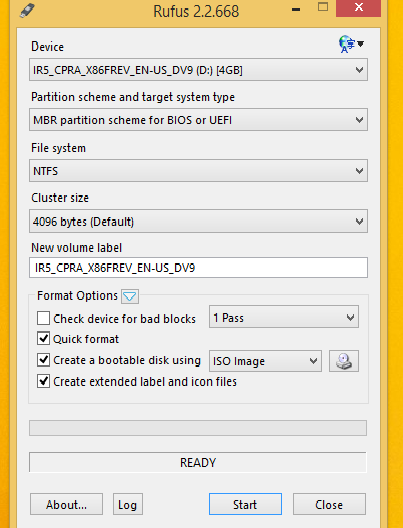
To turn a .ISO file into a bootable USB device, you can use the official Microsoft media creation tool mentioned on the above-linked page. However, a freeware program called Rufus is actually easier and faster. Plus, it lets you format the USB drive in GPT format, which may be useful if your PC's hard disk is also in the same format.
You'll find Rufus at https://rufus.akeo.ie/ and the download is only around 1 MB. It's portable so there's nothing to install, and the program is malware-free according to VirusTotal and Web of Trust.
For formatting USB sticks, and especially for creating a bootable USB pen drive from a .ISO file, Rufus is definitely a useful addition to your PC toolkit.
and Your pan-drive Bootable and go bois setting.Select Pan Drive Frist Boot device .
Comments