To day we tell ,CCNA( Course of Certified Network Associate).by Cisco, and 18-Networking-Solutions Provide information form CCNA Site,Some experts, and Some networking institute
1.Connectivity
2. Communication
Insertion of carrier (Stone) into information for covering long distance is called “Modulation”. And distraction of carrier unwanted information is called “Demodulation
1) Introduction
2) OSI (Open System Interconnection) Reference
Model
3) Network Devices
·
Types of Communication
·
Cards
·
LAN & WAN Concept
4) IP Addressing & Concepts
·
IPv4
·
IPv6
·
Subneting
·
Superneting
·
Variable Length Subnet
Scheme (VLSM)
·
And Operation
5) C.D.P
6) IOS Boot up Sequence
·
IOS
·
Upgrading
·
Dual (Booting)
7) IP Routing
·
Static Route
·
RIP (Routing
Information Protocol)
·
IGRP (Internet Gateway
Routing Protocol)
·
EIGRP (Enhance
Internet Gateway Routing Protocol)
·
OSPF (Open Shortest
Path First)
8) Switching
·
VLAN (Virtual Local
Area Network)
·
STP (Spanning Tree
Protocol)
9) ACL (Access Control List)
10) WAN (Wide Area Network) Router as a
Switch
11) Frame Relay
12) NAT & PAT Private
& Public
13) WLAN (Wireless Local Area Network)
14) VOIP (Voice Over Internet Protocol)
15) Cabling
Introduction-
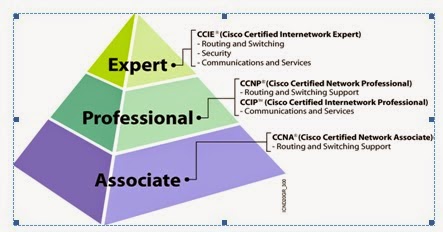
(Cisco Certified Network Associate)
Cisco is company of network,and many company are list like . there are many companies i.e. Cisco, Motorola, Simons, Microsoft,
but configurations are same. Cisco has 87% shares on infrastructure of IP. It
is said that if you send any small information on Internet, this is impossible
that this information do not pass through the Cisco Devices.
Certified
- Connectivity
- Communication
Associate
this is level in this line.Associate is the first level
Network
Our whole lab is aroud the one word i.e. "network".
" Connectivity of two or more than two devices.so that you can communication with each other,you can exchange the sources or share the information is called networking" it has two parts:
2. Communication
Medium may any (copper, wire and
wave) for the connectivity and communication. Connectivity is due to the
Hardware and communication is due to the Software.
Example
There is a telephone line
connected to your home telephone set from PTCL exchange. Is this a network? No,
because there is only connectivity but not communication. If an other person
talks with you, it is communication. Here the both parts fulfil the definition.
Now, you can say the “Network”.
Avoid
Wrong Concept
If you use the modem in between
the telephone exchange and your computer, then modem converts the analog
signals into digital to analog signals, this concept is wrong.
Insertion of carrier (Stone) into information for covering long distance is called “Modulation”. And distraction of carrier unwanted information is called “Demodulation
Comments